Internet of Things
Summary
The Internet of Things is an increasing number of objects that historically have not required the Internet to function, but are now integrating Internet connectivity in an attempt to form a more connected world. This article discusses the history of the Internet in order to frame the emergence of the Internet of Things. Some unique Internet of Things applications are provided to show the potential for these new Internet-connected devices. However, there are many obstacles that remain in the way of the Internet of Things. With the help of Electrical and Computer Engineers, these obstacles must be overcome before the Internet of Things can become truly mainstream.
Introduction
Have you ever walked out of your house, only to discover that you left your keys behind? What usually follows is a frantic search of pockets, bags, car seats and couch cushions. What you need is a smart key ring. Simply clip an extra fob to your key ring and the next time your keys go missing, you only need to pull out your smartphone. Your phone can then tell you how close you are to your keys or even make the key ring fob beep to help you find your keys quickly and with as little stress as possible.
In recent years there has been a trend of simple items and appliances being replaced with new “smart”, Internet-connected versions of themselves. This key ring is a perfect example of a “dumb” object, the classic metal key ring, being replaced by a “smart” object, the key ring that helps you find it.
This trend is known as the rise of the Internet of Things and it’s not just limited to key rings. There are smart devices that help you monitor your health, heat your home and even track the state of the environment.
Despite the promise of these new objects, there still remain significant challenges that prevent them from becoming truly ubiquitous. Many of these challenges lie in the fields of Electrical and Computer Engineering and will be solved by what students are learning today.
History of the Internet of Things
The concept of the Internet of Things (IoT) has been around since 1984, when it was first described by Ken Sakamura (Zhou, 2013), but it did not get its name until 1999 when Kevin Ashton officially coined the term (Mukhopadhyay, 2014). However to fully understand the Internet of Things it is first necessary to understand the history of the Internet. The Internet’s history can be split into three separate time periods, frequently referred to as the three waves of the Internet (Zhou, 2013). The first wave, the Internet of computers, is what many still think of as the Internet today. The Internet of computers is the system that has connected over a billion desktop computers together since the 1990s (Goldman Sachs, 2014). Then, technology advanced and computers began to be embedded into things that did not traditionally contain computers. This was the second wave of the Internet, now available on new devices such as mobile phones. These two waves focused on connecting 2.2 billion people (in 2011) together via the Internet, but the third wave of the Internet will take the next step: it will connect devices without requiring any human interaction (Mukhopadhyay, 2014; Zhou, 2013). This third wave is known as the Internet of Things.
The Internet of Things describes the network formed by “smart devices”, such as the smart key ring described at the start of this article. A smart device will usually have some sensors, a microprocessor and potentially a user interface, if human interaction is sometimes required. These devices also must have a method of connecting to the Internet. Frequently this will be a wireless technology, like WiFi or Bluetooth, but some smart devices also connect via wired technologies, such as Ethernet. It is the job of ECE engineers to determine how to design these new components and combine them into these new “smart devices”.
Internet of Things Applications
The Internet of Things has many consumer applications besides the smart key ring. Among them are popular devices such as health wristbands, like the FitBit, that track the wearer’s physical activity and sleep patterns. There are also smart thermostats that control heating and cooling in order to lower your energy bill. There are even smart light bulbs that can be remotely controlled or can control themselves based on the time, weather or if someone is in the room. While these consumer-facing products are becoming more and more prevalent, there are also a wealth of non-consumer products that are beginning to adapt to the Internet of Things.
Internet of Things Application: The Smart Grid
Nearly all of modern technology revolves around having constant access to electricity. This access has been provided to the public via the electric grid. While the current electric grid system works, there are many benefits to be gained by replacing it with a smarter and more connected version, appropriately named the Smart Grid.
The electric grid is tasked with taking power from power plants, delivering it to users and transforming it so it meets their needs. This is because the power needed by a large factory is much different than the power needed in a family’s residence (Sclater, 2003). These users have different needs at different times and the grid operators must deliver power where it is needed.
It is possible to determine which parts of the grid are lacking power and which parts have excess power at a given point in time, but it takes time to adjust to meet these needs. For instance if power is lacking, then a generating station may need to come online to make up the difference. This takes time and costs money, so any method to make this process more efficient saves both power providers and consumers money. Currently many grid operators use statistical methods to predict future demands, but this is not a foolproof system (Hersent, 2012).
The Smart Grid will attempt to improve the electric grid by collecting current data instead of using statistics based on historical data. This will be accomplished in part by smart meters. Smart meters are internet-connected electric meters that will allow constant monitoring which can immediately be shared with power grid operators (Zhou, 2013). These meters can also track a single consumers historical data, which can be shared with grid operators. By aggregating the data from all of their customers, grid operates will be able to make decisions based on their customers’ current usage patterns, not statistical estimates.
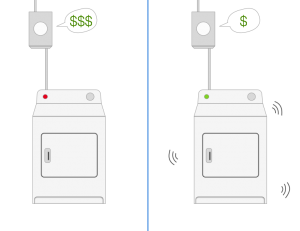
Another benefit of the smart grid is that it can work with other Internet of Things devices to further amplify benefits. For example, a smart clothes dryer could be scheduled to run when demand on the grid is low. It could also communicate its expected power needs with the grid. This combination of constant monitoring and smart application awareness benefits both the grid operators and consumers (Hersent, 2012). Grid operators now have better information that allows them to make well-informed decisions and to potentially automate new aspects of grid management. Since smart appliances run at off-peak times, their owners will pay less for the electricity.
Figure 1
Internet and Smart Grid-Connected Clothes Dryer. Source: Stephen Panaro.
Electrical and Computer Engineers play an important part in advancing the smart grid. They will need to design, develop and test the new smart power meters. They must determine how they will communicate with the grid as well as what information is useful to track. Any smart appliances, like the clothes dryer, will need engineers to determine how they will communicate with the grid and what methods will be used to estimate their future power usage.
Internet of Things Application: Visible Light Communication
It is not uncommon to see smart light bulbs that can be controlled from a smartphone. They can dynamically change color and turn themselves on and off at scheduled times. However, there is another type of smart light bulb that solves a completely different problem.
Most wireless communication, including Bluetooth and WiFi, occurs in the radio frequency (RF) spectrum. Unfortunately transmission in the RF spectrum is limited due to regulation and interference (Lo, 2004). Since more and more devices have a need for wireless communication, especially with the rise of the Internet of Things, the RF spectrum is becoming crowded. One solution to this is to look into different spectrums for communication, such as the visible light spectrum. The technology that achieves this is known as Visible Light Communication (VLC).
VLC is the process of transmitting data by using visible light waves instead of the traditional radio waves (Lo, 2004). VLC is appealing because it is in an unregulated bandwidth, unlike RF, which makes adoption easier. VLC also has a potential 300 THz of bandwidth, allowing for multi-gigabit per second communications (Rajagopal, 2012).
VLC is a promising technology on its own, but implementing it in smart light bulbs is where real benefits will be found. Light bulbs already are used in many indoor spaces to provide light, but with the right technology they could be replaced by smart light bulbs. These bulbs would provide the same light but also wireless Internet connectivity (Kavehrad, 2010). This would result in less RF interference, less dedicated communications hardware and less wasted power.
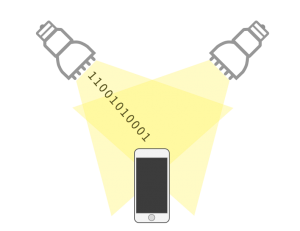
Figure 2
VLC Light Bulbs Provide Light and Data. Source: Stephen Panaro.
There are already a few installations of VLC light bulbs. Phillips installed smart light bulbs in a Dusseldorf grocery store and developed a smartphone application. When used together the application uses the lights to locate the user in a supermarket and helps them find products (LaMonica, 2014). While this is only one-way communication, it highlights the viability and simplicity of VLC light bulbs.
It will be the job of Electrical and Computer Engineers to further develop VLC light bulbs and find new applications for them. Additionally, there still remains significant research to do to establish a method of communicating from device to light bulb because VLC can’t be used to communicate in both directions (Kavehrad, 2010).
What’s Next for the Internet of Things?
In 2008, the number of devices connected to the Internet surpassed the number of humans (Evans, 2011) and the trend hasn’t changed much since then. While there are already a great number of devices connected to the Internet of Things, that number will only increase in the coming years. While the prospect of more interconnected devices is exciting, there are many obstacles that still remain for Electrical and Computer Engineers to overcome before the Internet of Things can reach its full potential.
The high number of potential internet-connected devices will cause problems. This may mean that current protocols and methods for connecting to the Internet no longer suffice. Additionally, all of these new devices will be generating data from the sensors at a very high rate. It will be important to store that data and to ensure that it is stored accurately, so that it is trustworthy (Stankovic, 2014).
Standard computers connect to the Internet using a protocol known as the IP (the Internet Protocol). Part of the IP puts limits on how many devices can connect to the Internet. The influx of new Internet-connected Internet of Things devices will test this limit. Fortunately, there is a new version of the IP, IPv6, which should increase this limit enough to sustain the Internet of Things (Zhou, 2013). Along with increasing the number of devices that can connect to the Internet, IPv6 will allow them to communicate faster then ever before.
IPv6 won’t suffice for every Internet of Things device. The fact that many Internet of Things devices will operate on small amounts of power demands a low power alternative to IPv6. One solution to this is a technology named 6LoWPAN. Unlike IPv6, 6LoWPAN will not connect directly to the Internet. Rather it will connect to other nearby devices in what is known as a mesh network (Hersent, 2012). This technology will allow Internet of Things devices to save power while communicating with each other, but it does not prevent them from connecting to the Internet as well.
As with any software system, the Internet of Things is a target for hackers. However, unlike the traditional Internet, where a successful hacker may gain access to a social network account, hacking attacks on the Internet of Things pose a much larger risk. Where previous hackers mostly operated in the digital realm, the Internet of Things will introduce the risk of hackers operating in the physical world. The stakes are higher because these internet-connected objects will be able to collect sensitive sensor data about their environment and may even have the power to control it, for instance by unlocking a door or disabling a security system. This problem is further complicated because Internet of Things devices will be lightweight and will require lightweight security systems that are still robust enough to do their jobs (Stankovic, 2014). Fortunately, the area of system security is an active research topic in both Computer Science and Electrical and Computer Engineering disciplines.
One such area of research involves preventing hackers from gaining unauthorized access to data. Since Internet of Things devices will be connected to the Internet, they will be exposed to the same security risks that any normal website faces. Fortunately, since these smart devices will connect to the Internet by the same means as current computers, they can use the same tried and true security measures (Ning, 2013). On top of this, any advances in computer security will also benefit Internet of Things devices.
Another area of research involves defending against attacks intended to take Internet of Things devices offline. These attacks typically are achieved in two ways. First a denial of service attack could overwhelm the device by sending it much more data than it is capable of processing. This could potentially stop it from performing its non-Internet-connected function. Second a jamming system could be used to prevent wireless devices from accessing the Internet by interfering with their wireless communications (Ning, 2013). Both of these attacks reduce the smart device’s functionality, either back to that of a dumb device or even to the point where the device fails to function.
Since smart devices will know more personal data about their users than any device before, their security is a high priority for the Electrical and Computer Engineers developing them. Consumers need to be able to trust the devices and the engineers must work to preserve that trust.
Conclusion
The Internet of Things is an exciting area of research and technology that is both producing new devices and expanding the capabilities of existing ones. While it is not yet widely adopted, it is approaching the mainstream at a rapid rate. With the help of Electrical and Computer engineers the remaining obstacles will be surmounted, the technology will continue to mature and the world will become more connected and efficient then ever before.
Bibliography
- Evans, D. (2011). The Internet of Things [INFOGRAPHIC]. Cisco Blogs. Retrieved from http://blogs.cisco.com/diversity/the-internet-of-things-infographic
- Goldman Sachs (Producer). (2014, 12 August). The IOT as the Third Wave of the Internet [Video File]. Retrieved from http://www.goldmansachs.com/our-thinking/outlook/iot-video.html
- Hersent, O., & Boswarthick, D. (2012). The Internet of Things: Key Applications and Protocols. Chichester, West Sussex: Wiley. OCLC WorldCat Permalink: http://www.worldcat.org/oclc/773301003
- Kavehrad, M. (2010). Sustainable Energy-Efficient Wireless Applications Using Light. IEEE Communications Magazine, pp. 66-73. DOI: 10.1109/MCOM.2010.5673074
- Lo, S. C. (2010). Visible Light Communications. The Hong King
University of Science and Technology, Hong Kong. Retrieved from http://bemri.org/publications/visible-light-communication/284-visible-light-communications.html - Mukhopadhyay, S. (2014). Internet of things: Challenges and Opportunities. OCLC WorldCat Permalink: http://www.worldcat.org/oclc/871268087
- Ning, H. (2013). Unit and Ubiquitous Internet of Things. Boca Raton: CRC Press, Taylor & Francis Group.OCLC WorldCat Permalink: http://www.worldcat.org/oclc/841172192
- Rajagopal, S., Roberts, R. D., & Lim, S. K. (2012). IEEE 802.15. 7 visible light communication: modulation schemes and dimming support. Communications Magazine, IEEE, 50(3), 72-82. DOI: 10.1109/MCOM.2012.6163585
- Sclater, N., & Traister, J. (2003). Power Generation and Transmission. In Handbook of Electrical Design Details (2nd ed.). New York: McGraw-Hill. OCLC WorldCat Permalink: http://www.worldcat.org/oclc/53448113
- Stankovic, J.A., “Research Directions for the Internet of Things,” Internet of Things Journal, IEEE , vol.1, no.1, pp.3,9, Feb. 2014 DOI: 10.1109/JIOT.2014.2312291
- Zhou, H. (2013). The Internet of Things in the Cloud: A Middleware Perspective. Boca Raton: CRC Press, Taylor & Francis Group. OCLC WorldCat Permalink: http://www.worldcat.org/oclc/812917056