Senior Fall
Simple Web-Based To-Do List
The objective of this project was to use Python to create something of our choosing. I decided to build a web-based to-do list application that integrated user accounts, task management, and a dynamic calendar view, similar to the known Google Calendar.
Users can create an account, manage personalized tasks, and visualize their schedules on a dynamic calendar using HTTP requests that showcase the server-client model and the flow of data on the web. Sessions secure user data and the logical routes serve dynamic content, while providing a simple UI to allow users to navigate easily.
This project requires the use of a broad range of topics from computer communication networks, web development, and software design. The project utilizes Python and the Flask framework. The project also utilizes SQLAlchemy and SQLite for data persistence, Bootstrap for a polished interface, and FullCalendar for the dynamic client-side interactivity.
Junior Spring
Web Security Crash Course
As part of the Spring 2024 MassCyberCenter Mentorship cohort, I was paired with an industry professional to work on a personal project exploring cybersecurity risks. The objective of this project was to create an educational piece regarding cyber security. I spent the semester researching web security and exploring common security flaws in websites. This project demonstrates these vulnerabilities, explains mitigations for these concerns, as well as lists overall safe practices for companies to implement in their workspaces. The intended audience is not only companies, but students studying computer science and software.
Autonomous Car Bot
The objective of this project was to design and build for a customer. The requirements include using sensors to follow a colored line (blue, red, yellow), operate in low-light, detect and avoid collisions, and communicate with a companion bot over WiFi servers to navigate the course.
Our team has successfully managed costs of the project, met deadlines, created a bot spec, and implemented various sensors. The bot drives forward, backwards, spins, pivots, and turns 90, 180, and 360 degrees. It can also detect collisions in day and night time, communicate with HTTP protocol over WiFi, as well as follow the colored path.
To accomplish this, we have used a variety of tools. The Arduino IDE allows us to manage our code implementations, 9V batteries to make our bot “wireless” (AKA not connected to a laptop or power supply!), a multitude of wires, resistors, and the L293D Integrated Circuit to use H-Bridge mechanics.
Tools: Arduino, Arduino IDE, Circuits + Circuit Design, C++ Programming
Junior Fall
Pipelined Processor – VHDL
The objective of this project was to create a pipelined processor using LEGv8. This included implementing forwarding and hazard detection in the pipelined CPU. I created and connected multiple entities to create a functional pipelined CPU. The CPU implements the entirety of the subset of ARM v8-64 bit ISA instructions as follows: ADD, ADDI, AND, ANDI, B, CBZ, CBNZ, LDUR, LSL, LSR, NOP, ORR, ORRI, STUR, SUB, and SUBI.
Design Logic: For the Pipelined CPU, I used a structural architecture. The entity uses a multitude of other VHDL components to implement the CPU. This includes multiple MUX devices, an ALU, an ALUControl, a CPUControl, SignExtend, Left/Right Shift, AND2, OR2, and many more necessary entities. These components are used together to execute certain instructions, as well as implement data flow. Moving each piece of information to the next part of the pipeline requires communication (wires) through and connecting each component. The forwarding and hazard detection are also used as components that take in some of the signals and pass them out to different parts of the pipeline (forwarding) or altering their values (hazard detection) when necessary.
Tools: Visual Studio Code, GTKWave
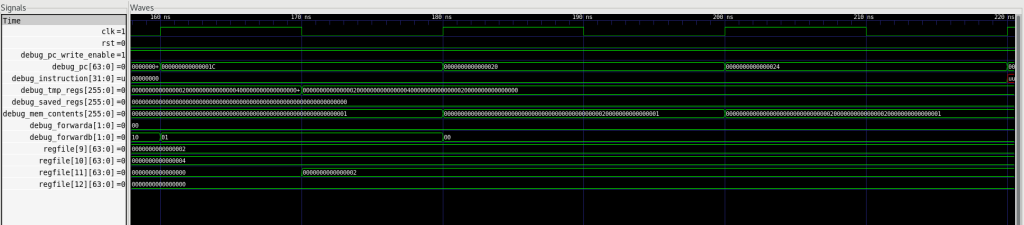

LDUR X9, [XZR,0] → X9 = M[XZR, 0] (X9 gets memory value)
ADD X9, X9,X9 → X9 = X9 + X9
ADD X10, X9,X9 → X10 = X9 + X9
SUB X11, X10,X9 → X11 = X10 - X9
STUR X11, [XZR,8] → M[XZR + 8] = X11 (memory gets X11 value)
STUR X11, [XZR,16] → M[XZR + 16] = X11 (memory gets X11 value)
NOP
NOP
NOP
NOPPhysics 11 Learning Assistant Research
During my time as a Physics 11 Learning Assistant, I had the pleasure of working alongside two other student-led roles, Section Coaches and Lab TAs. These three roles held different responsibilities. Learning Assistants assist a group of ~25 students during 75-minute lecture, Section Coaches host ~30 students during 50-minute recitation, and Lab TAs guide ~15 students during 2-hour lab. In our STEM Learning Assistants education course, my partners and I explored a research question, “Do student and facilitator questions differ / change in the different environments this course provides? Is this change reflective of the three roles the course provides for student learning?”. After a month of conducting and collecting research, we compiled a poster and paper containing our findings.
Cyber Threat Memo – Final Paper
As the final project in “Cyber in the Civilian Sector”, we were prompted with an imaginary Cyber Threat and requested to respond in a Memo. The following questions are addressed in the memo, alongside my personal recommendations: “(1) How Ghana, Nigeria, and South Africa should respond to the FuzzyBear ransom demands; (2) What action to take towards the Chinese government in light of the espionage allegations; (3) Whether to block access to Meta services in AU member nations because of concerns about espionage and, if so, how best to do that, and (4) What to do about the mysterious devices encircling portions of the 2Africa cable in certain countries and whether to continue using the 2Africa system at all.”
Sophomore Spring
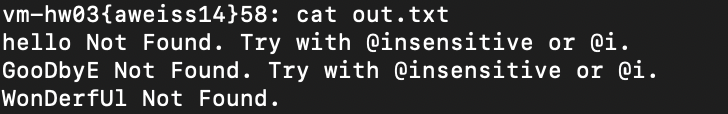
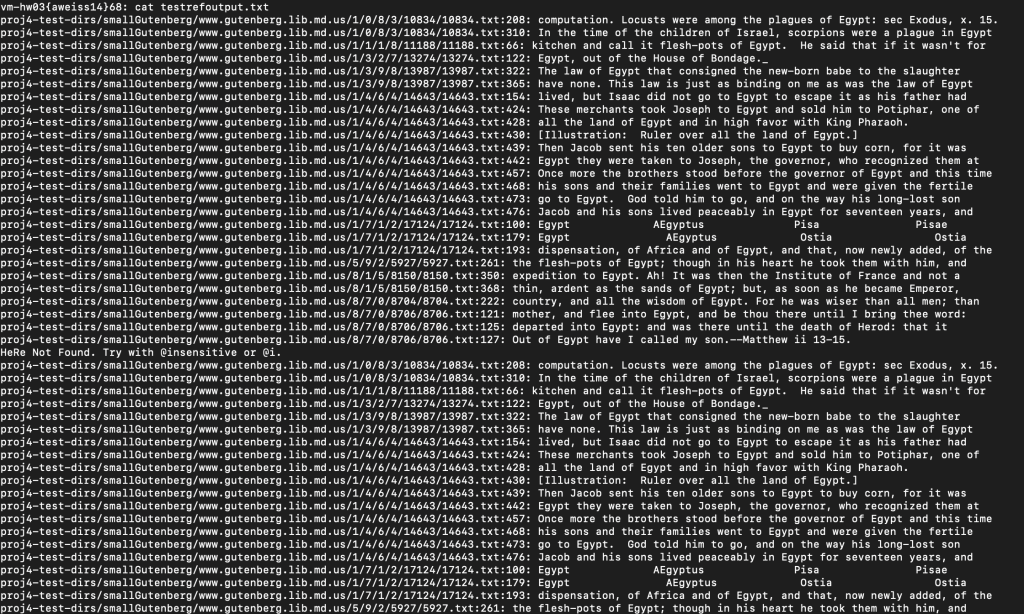
Gerp – C
The objective of this project was to create a replication of the Linux command “grep”. Grep is the linux search program that can search through all files in a directory for a certain sequence of characters. In our everyday lives, this is similar to Mac spotlight search, or even google search engine. The program when given a directory to search, will go through all subdirectories and through all of the files in each directory searching for the user provided word. Once the word in the query is provided, this program returns the filepath, line number, and the whole line where the word was located to an output file. There are 4 different commands: case sensitive search, case insensitive search, changing the output file, and quitting the program.
Data Structures: trees, vectors, simulated hash table with structs
Goal: Sufficiently replicate the program, as well as manage time and space complexity
Result: Placed 3rd on class leaderboard for Time + Space Complexity efficiency!
Space: 2.18 GB, Index time: 14.89 sec, Query Time: 1.14 sec