The Security Implications of Accelerator-rich Architectures and the Thermal Side Channel
With the rise of the Internet of Things, an ever-growing number of devices contain processors. These processors often contain hardware accelerators that implement a specific task, such as encryption, video encoding, or digital signal processing.In such systems, processing-activity within a specific accelerator indicates that the system is currently executing that core’s given task (e.g. encryption) and will result in a corresponding increase in temperature at the location of the given core. This work leverages the spatial increase in temperature in order to determine what accelerator(s) are active in order to reveal system state. Current results show that the leaked thermal information can be used for reverse engineering software and even malware detection. An overview of the developed methodology is shown below:
Compensating for heat diffusion via power estimation
Determining core activity using the thermal channel directly is problematic because heat tends to diffuse across the entire processor, making it hard to determine which cores are active. The images below show a thermal profile (left) and the corresponding estimated power profile produced by our power-estimation technique (right). The activity of each core is far more apparent when viewing the estimated power profile than when viewing the thermal profile.
Reverse Engineering Software
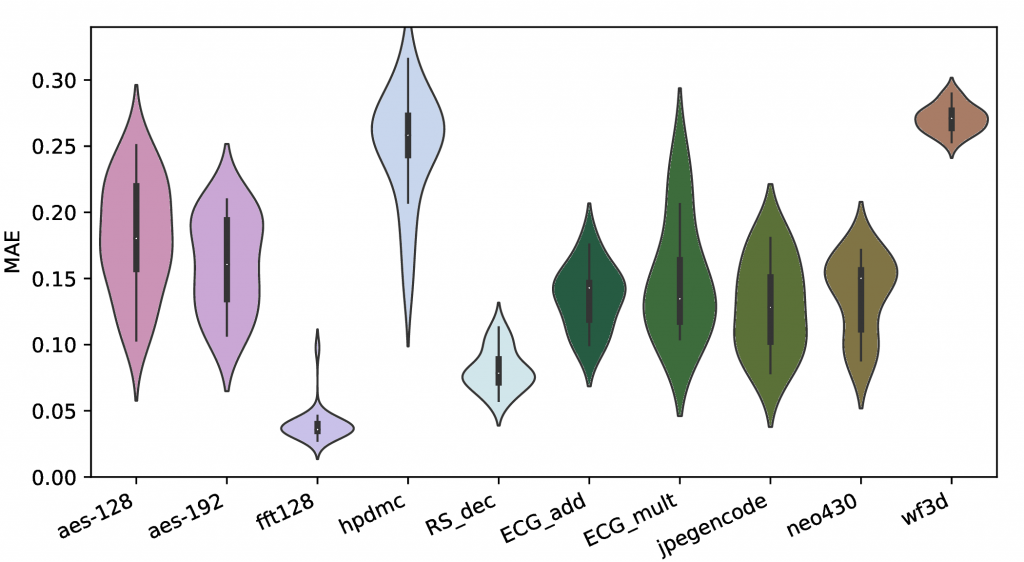
One possible application for the thermal side-channel is the reverse engineering of software. Estimated power profiles are used to train Neural Networks that predict the activity factor of each core. The figure below shows the Mean Average Error of the models for each core across a variety of systems.
Malware Detection
Information leaked over the thermal profile can also be used to detect anomalies in core activity factors that would be indicative of the presence of malware. Parametric statistical models were used to detect the presence of malware.
Future work
Current results are promising and have demonstrated the utility of the thermal side-channel. Future work will expand on these results by 1) using sensor fusion to incorporate information from other side-channels into existing models; 2) characterizing the theoretical bound on the information-rate of the thermal side-channel; and 3) validating and tuning the aforementioned techniques on a thermal test-bed developed using a Field Programmable Gate Array(FPGA).
Publications
-
M Hempstead, D Werner, E Miller, K Juretus, I Savadis – US Patent 11,880,463, 2024
- David Werner, Kyle Juretus, Ioannis Savidis and Mark Hempstead. Machine Learning on the Thermal Side-Channel: Analysis of Accelerator-rich Architectures. The 36th IEEE International Conference on Computer Design (ICCD), Oct 2018. [PDF]
- D. Werner, M. Hempstead, K. Juretus, and I. Daulagala, “The Vulnerability of Specialized Architectures to Temperature Side-Channel Information Leakage,” Boston Area Architecture Workshop (BARC), Jan. 2016.